Fillable Printable Information security policy - UK
Fillable Printable Information security policy - UK

Information security policy - UK

Policy
Information Security Policy
Jethro Perkins
Information Security Manager
For latest version and information about, see lse.ac.uk/policies and search by title.1

Foreword to the Information Security Policy
The current era, often referred to as the “information age”, has seen human beings generate, store
and exchange information at an unprecedented rate. It has profoundly altered the terms by which we
interact with each other, not just as individuals, but also within and between institutions, societies and
nations.
We have accrued great benefits from this new era, but it brings with it profound challenges in the
areas of security and privacy, which have been reflected in the growth of legislation around the globe
concerning the holding of information.
As a leading higher education institution committed to both high quality teaching and research, LSE
has an ethical, legal and professional duty to ensure that the information it holds conforms to the
principles of confidentiality, integrity and availability; in other words, that the information we hold or are
responsible for is safeguarded where necessary against inappropriate disclosure; is accurate, timely
and attributable; and is available to those who should be able to access it.
The Information Security Policy below provides the framework by which we take account of these
principles. Its primary purpose is to enable all LSE staff and students to understand both their legal
and ethical responsibilities concerning information, and empower them to collect, use, store and
distribute it in appropriate ways.
This policy is the cornerstone of LSE’s on-going commitment to enhance and clarify our information
security procedures. It has, in consequence, my full support, and I ask all LSE staff and students to
read it and abide by it in the course of their work.
Professor Craig Calhoun
Director
London School of Economics and Political Science
July 2013
For latest version and information about, see lse.ac.uk/policies and search by title.2
1 Introduction
The confidentiality, integrity and availability of information, in all its forms, are critical to the on-going
functioning and good governance of LSE. Failure to adequately secure information increases the risk
of financial and reputational losses from which it may be difficult for LSE to recover.
This information security policy outlines LSE’s approach to information security management. It
provides the guiding principles and responsibilities necessary to safeguard the security of the
School’s information systems. Supporting policies, codes of practice, procedures and guidelines
provide further details.
LSE is committed to a robust implementation of Information Security Management. It aims to ensure
the appropriate confidentiality, integrity and availability of its data. The principles defined in this policy
will be applied to all of the physical and electronic information assets for which the LSE is responsible.
LSE is specifically committed to preserving the confidentiality, integrity and availability of
documentation and data supplied by, generated by and held on behalf of third parties pursuant to the
carrying out of work agreed by contract in accordance with the requirements of data security standard
ISO 27001.
1.1 Purpose
The primary purposes of this policy are to:
1. Ensure the protection of all LSE information systems (including but not limited to all
computers, mobile devices, networking equipment, software and data) and to mitigate the
risks associated with the theft, loss, misuse, damage or abuse of these systems.
2. Make certain that users are aware of and comply with all current and relevant UK and EU
legislation.
3. Provide a safe and secure information systems working environment for staff, students and
any other authorised users.
4. Ensure that all users understand their own responsibilities for protecting the confidentiality
and integrity of the data that they handle.
5. Protect LSE from liability or damage through the misuse of its IT facilities.
6. Respond to feedback and update as appropriate, initiating a cycle of continuous improvement.
1.2 Scope
This policy is applicable to, and will be communicated to, all staff, students, other members of the
School and third parties who interact with information held by the LSE and the information systems
used to store and process it. This includes, but is not limited to, any systems or data attached to the
LSE data or telephone networks, systems managed by LSE, mobile devices used to connect to LSE
networks or hold LSE data, data over which LSE holds the intellectual property rights, data over which
LSE is the data owner or data custodian, communications sent to or from the LSE.
1.3 Definitions
LSE Data, for the purposes of this policy, is data owned, processed or held by LSE, whether primary
or secondary, irrespective of storage location. It is used interchangeably with the term ‘information’.
For latest version and information about, see lse.ac.uk/policies and search by title.4

2 Policy
2.1 Informationsecurity principles
The following information security principles provide overarching governance for the security and
management of information at LSE.
1. Information should be classified according to an appropriate level of confidentiality, integrity
and availability (see Section 2.3. Information Classification) and in accordance with relevant
legislative, regulatory and contractual requirements and LSE policy (see Section 2.2. Legal
and Regulatory Obligations).
2. Staff with particular responsibilities for information (seeSection 3. Responsibilities) are
responsible for ensuring the classification of that information; for handling that information in
accordance with its classification level; and for any policies, procedures or systems for
meeting those responsibilities.
3. All users covered by the scope of this policy (see Section 1.2. Scope) must handle information
appropriately and in accordance with its classification level.
4. Information should be both secure and available to those with a legitimate need for access in
accordance with its classification level.
5. Information will be protected against unauthorized access and processing in accordance with
its classification level.
6. Breaches of this policy must be reported (see Sections 2.4. Compliance and 2.5. Incident
Handling).
2.2 Legal & Regulatory Obligations
The London School of Economics has a responsibility to abide by and adhere to all current UK and
EU legislation as well as a variety of regulatory and contractual requirements.
A non-exhaustive summary of the legislation and regulatory and contractual obligations that contribute
to the form and content of this policy is provided in Appendix A. Related policies will detail other
applicable legislative requirements or provide further detail on the obligations arising from the
legislation summarised below.
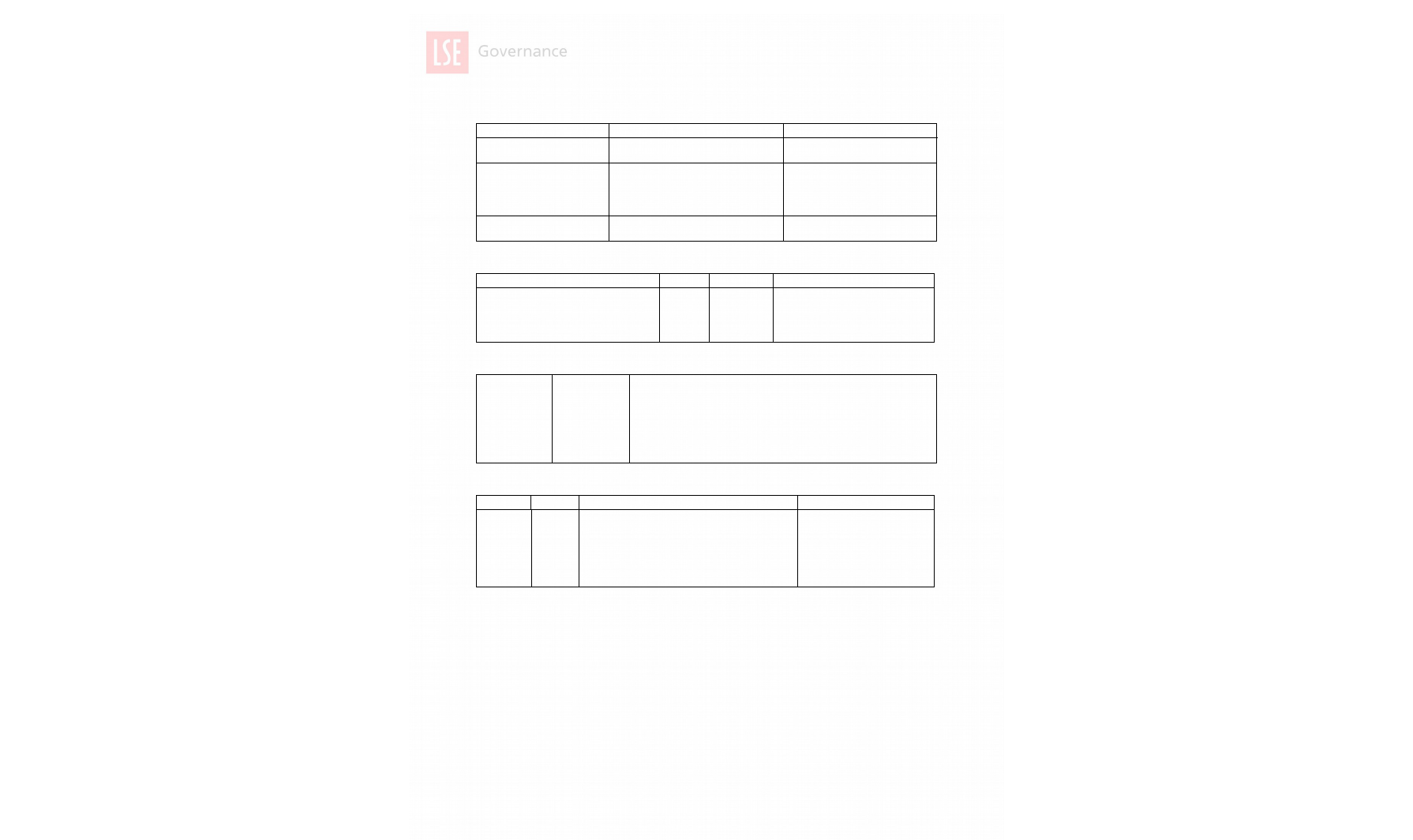
2.3 InformationClassification
The following table provides a summary of the information classification levels that have been
adopted by LSE and which underpin the 8 principles of information security defined in this policy.
These classification levels explicitly incorporate the Data Protection Act’s (DPA) definitions of
Personal Data and Sensitive Personal Data, as laid out in LSE’s Data Protection Policy, and are
designed to cover both primary and secondary research data. Detailed information on defining
information classification levels and providing appropriate levels of security and access is provided in
the Data Classification Standard .
Security
Level
Definition Examples FOIA2000 /
DPA1998 status
1. ConfidentialNormally
accessible
only to
specified
members of
LSE staff
DPA-defined Sensitive personal data
(racial/ethnic origin, political opinion, religious
beliefs, trade union membership,
physical/mental health condition, sexual life,
criminal record) including as used as part of
primary or secondary research data;
Subject to
significant scrutiny
in relation to
appropriate
exemptions/ public
interest and legal
For latest version and information about, see lse.ac.uk/policies and search by title.6
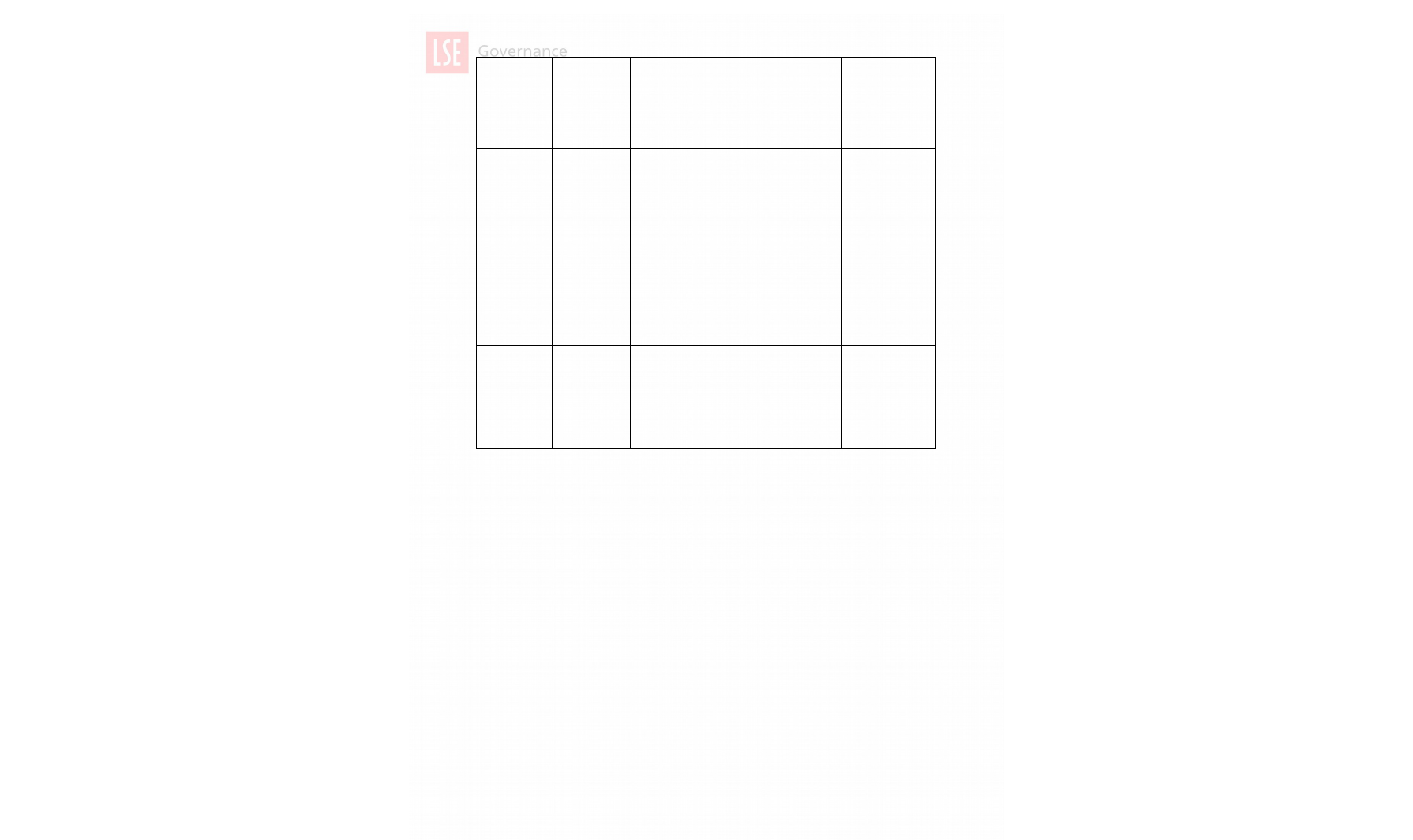
individuals’ bank details;
passwords;
large aggregates of personally identifying
data (>1000 records) including elements
such as name, address, telephone number.
considerations.
2. Restricted Normally
accessible
only to
specified
members of
LSE staff or
the student
body
DPA-defined Personal Data (information that
identifies living individuals including home /
work address, age, telephone number,
schools attended, photographs);
reserved committee business;
draft reports, papers and minutes;
systems.
Subject to
significant scrutiny
in relation to
appropriate
exemptions/ public
interest and legal
considerations.
3. Internal Use Normally
accessible
only to
members of
LSE staff and
the student
body
Internal correspondence,
final working group papers and minutes,
committee papers,
information held under license
Subject to scrutiny
in relation to
appropriate
exemptions/ public
interest and legal
considerations
4. Public Accessible to
all members of
the public
Annual accounts,
minutes of statutory and other formal
committees,
pay scales etc.
Information available on the LSE website or
through the LSE’s Publications Scheme.
Freely available
on the website or
through the LSE’s
Publication
Scheme.
2.4 Compliance, Policy Awareness and Disciplinary Procedures
Any security breach of LSE’s information systems could lead to the possible loss of confidentiality,
integrity and availability of personal or other confidential data stored on these information systems.
The loss or breach of confidentiality of personal data is an infringement of the Data Protection Act
(1998), contravenes LSE’s Data Protection Policy, and may result in criminal or civil action against
LSE. The loss or breach of confidentiality of contractually assured information may result in the loss of
business, financial penalties or criminal or civil action against LSE. Therefore it is crucial that all users
of the School’s information systems adhere to the Information Security Policy and its supporting
policies as well as the Information Classification Standards.
All current staff, students and other authorised users will be informed of the existence of this policy
and the availability of supporting policies, codes of practice and guidelines.
Any security breach will be handled in accordance with all relevant School policies, including the
Conditions of Use of IT Facilities at the LSE and the appropriate disciplinary policies.
2.5 Incident Handling
If a member of the School (staff or student) is aware of an information security incident then they must
report it to the Information Management and Technology Service Desk at IT.Servicedesk@lse.ac.uk
or telephone 020 7107 5000.
If necessary, members of the School can also use LSE’s Whistle Blowing (Public Interest Disclosure)
policy (see //www2.lse.ac.uk/intranet/staff/brightIdeas/haveYourSay/whistleBlowing/Home.aspx.)
For latest version and information about, see lse.ac.uk/policies and search by title.7

2.6 Supporting Policies, Codes of Practice, Procedures and Guidelines
Supporting policies have been developed to strengthen and reinforce this policy statement. These,
along with associated codes of practice, procedures and guidelines are published together and are
available for viewing on LSE’s website. All staff, students and any third parties authorised to access
LSE’s network or computing facilities are required to familiarise themselves with these supporting
documents and to adhere to them in the working environment.
Supporting policies may be found at:
http://www.lse.ac.uk/intranet/LSEServices/IMT/about/policies/home.aspx
2.7 Review andDevelopment
This policy, and its subsidiaries, shall be reviewed by the Information Security Advisory Board (ISAB)
and updated regularly to ensure that they remain appropriate in the light of any relevant changes to
the law, organisational policies or contractual obligations.
Additional regulations may be created to cover specific areas.
ISAB comprises representatives from all relevant parts of the organisation. It shall oversee the
creation of information security and subsidiary policies.
The Information Security Manager will determine the appropriate levels of security measures applied
to all new information systems
For latest version and information about, see lse.ac.uk/policies and search by title.8
3 Responsibilities
Members of LSE:
All members of LSE, LSE associates, agency staff working for LSE, third parties and collaborators on
LSE projects will be users ofLSE information. This carries with it the responsibility to abide by this
policy and its principles and relevant legislation, supporting policies, procedures and guidance. No
individual should be able to access information to which they do not have a legitimate access right.
Notwithstanding systems in place to prevent this, no individual should knowingly contravene this
policy, nor allow others to do so. To report policy contraventions, please see Section 2.5: Incident
Handling
Data Owners / Guardians:
Many members of LSE will have specific or overarching responsibilities for preserving the
confidentiality, integrity and availability of information. These include:
Principal Investigators / Project administrators:
Responsible for the security of information produced, provided or held in the course of carrying out
research, consultancy or knowledge transfer activities. This includes ensuring that data is
appropriately stored, that the risks to data are appropriately understood and either mitigated or
explicitly accepted, that the correct access rights have been put in place, with data only accessible to
the right people, and ensuring there are appropriate backup, retention, disaster recovery and disposal
mechanisms in place.
Heads of Departments, Divisions, Centres:
Responsible for the information systems (e.g. HR/ Registry/ Finance) both manual and electronic that
support LSE’s work. Responsibilities as above (for Principal Investigators / Project administrators).
Departmental managers / Line managers:
Responsible for specific area of LSE work, including all the supporting information and documentation
that may include working documents/ contracts/ staff or student information.
Head of Research Division
Signs off LSE research contracts and is responsible for providing the assurance that any mandated
security measures for research data are met.
School Secretary
Responsible for LSE compliance with the Data Protection Act
Records Manager
Responsible for LSE’s Data Protection Policy, data protection and records retention issues.
IMT, Library IT and STICERD IT Staff:
Responsible for ensuring that the provision of LSE’s IT infrastructure is consistent with the demands
of this policy and current good practice.
Head of Security:
Responsible for physical aspects of security and will provide specialist advice throughout the LSE on
physical security issues.
Information Security Manager:
Responsible for this and subsequent information security policies and will provide specialist advice
throughout the School on information security issues.
Information Security Advisory Board
Responsible for the advising on and recommending information security policies to the Information
Technology Committee, assessing information security risks, identifying and implementing controls to
risks.
Information Technology Committee
Responsible for approving information security policies.
For latest version and information about, see lse.ac.uk/policies and search by title.9
Document control
Distribution list
Name Title Department
Nick Deyes Director of Information Management
Technology
IMT
Information Security
Advisory Board (ISAB)
Information Technology
Committee (ITC)
External document references
Title Version DateAuthor
Data Protection Policy 2.3 04/12/13 Dan Bennett
ISO/IEC 27001:2013 01/10/2013 ISO/IEC
Version history
Date Version Comments
12/03/13
08/07/13
15/05/15
30/06/15
01/07/15
3.0
3.1
3.5
3.6
3.7
Created single point of contact for incident reporting. Version
approved by ITC 11/03/13.
Incorporated foreword by Professor Craig Calhoun, LSE Director.
Restructured version for review by ISAB
Submitted to ITC 30/06/15. Endorsed.
Minor correction as required by ITC
Review control
Reviewer Section Comments Actions agreed
ITC 2.3 Information Classification: ‘Internal Use’ data
should be accessible to members of LSE staff
and the student body, not or.
Correction made.
For latest version and information about, see lse.ac.uk/policies and search by title.10

4 Appendix A: Summary of relevant
legislation
4.1 The Computer Misuse Act 1990
Defines offences in relation to the misuse of computers as:
1. Unauthorised access to computer material.
2. Unauthorised access with intent to commit or facilitate commission of further offences.
3. Unauthorised modification of computer material.
4.2 Data Protection Act 1998
Provides a safeguard for personal privacy in relation to computerised or other systematically filed
information; it regulates the use of personal data meaning information about living human beings. It is
an offence to process personal data except where they are:
1. Fairly and lawfully processed
2. Processed for limited purposes
3. Adequate, relevant and not excessive
4. Accurate and up to date
5. Not kept for longer than is necessary
6. Processed in line with your rights
7. Secure
8. Not transferred to countries outside the EEA without adequate safeguards
LSE has a Data Protection Policy which further governs the use of personal data.
4.3 The Freedom of Information Act 2000
The Freedom of Information Act 2000 (FOIA2000) is a general right of public access to all types of
recorded information held by public authorities in order to promote a culture of openness and
accountability.
4.4 Regulation of Investigatory Powers Act 2000
The Regulation of Investigatory Powers Act 2000 regulates the powers of public bodies to carry out
surveillance and investigation. It covers the interception and use of communications data and can be
invoked in the cases of national security, and for the purposes of detecting crime, preventing disorder,
public safety and protecting public health.
4.5 Defamation Act 1996
“Defamation is a false accusation of an offence or a malicious misrepresentation of someone's words
or actions. The defamation laws exist to protect a person or an organisation's reputation from harm.
i
”
4.6 Obscene Publications Act 1959 and 1964
The law makes it an offence to publish, whether for gain or not, any content whose effect will tend to
"deprave and corrupt" those likely to read, see or hear the matter contained or embodied in it. This
could include images of extreme sexual activity such as bestiality, necrophilia, rape or torture.
ii
i
For latest version and information about, see lse.ac.uk/policies and search by title.11

4.7 Protectionof Children Act 1978, Criminal Justice Act 1988, Criminal
Justice and Immigration Act 2008
The Protectionof Children Act 1978prevents the exploitation of children by making indecent
photographs of them and penalises the distribution and showing of such indecent photographs.
Organisations must take appropriate steps to prevent such illegal activities by their workers using their
digital systems and networks.
The definition of ‘photographs’ include data stored on a computer disc or by other electronic means
which is capable of conversion into an image.
It is an offence for a person to […] distribute or show such indecent photographs; or to possess such
indecent photographs, with a view to their being distributed or shown by himself or others.
Section 160 of the Criminal Justice Act 1988 made the simple possession of indecent photographs of
children an offence. Making an indecent image of a child is a serious arrestable offence carrying a
maximum sentence of 10 years imprisonment. Note: The term "make" includes downloading images
from the Internet and storing or printing them out.
iii
4.8 Terrorism Act 2006
The Terrorism Act 2006 makes it an offence to write, publish or circulate any material that could be
seen by any one or more of the persons to whom it has or may become available, as a direct or
indirect encouragement or other inducement to the commission, preparation or instigation of acts of
terrorism.
It also prohibits the writing, publication or circulation of information which is likely to be useful to any
one or more persons in the commission or preparation of terrorist acts or is in a form or context in
which it is likely to be understood by any one or more of those persons as being wholly or mainly for
the purpose of being so useful.
In addition, it prohibits the glorification of the commission or preparation (whether in the past, in the
future or generally) of terrorist acts or such offences; and the suggestion that what is being glorified is
being glorified as conduct that should be emulated in existing circumstances.
For latest version and information about, see lse.ac.uk/policies and search by title.12